Stanford University Pressured to Pay Ransom so Hackers Don’t Leak Sensitive Data Stolen in Recent Attack

Akira ransomware operators are threatening to leak a trove of sensitive data stolen in an attack on the Stanford University’s Public Safety Department.
The Stanford University Department of Public Safety (SUDPS) provides law enforcement, security, safety, crime prevention and emergency services on the Stanford campus.
Akira ransomware operators recently made an entry on their retro-style data leak site, claiming they’re sitting on 430 GB of “private information [and] confidential documents,” according to a screenshot shared by The Stanford Daily (embedded below).
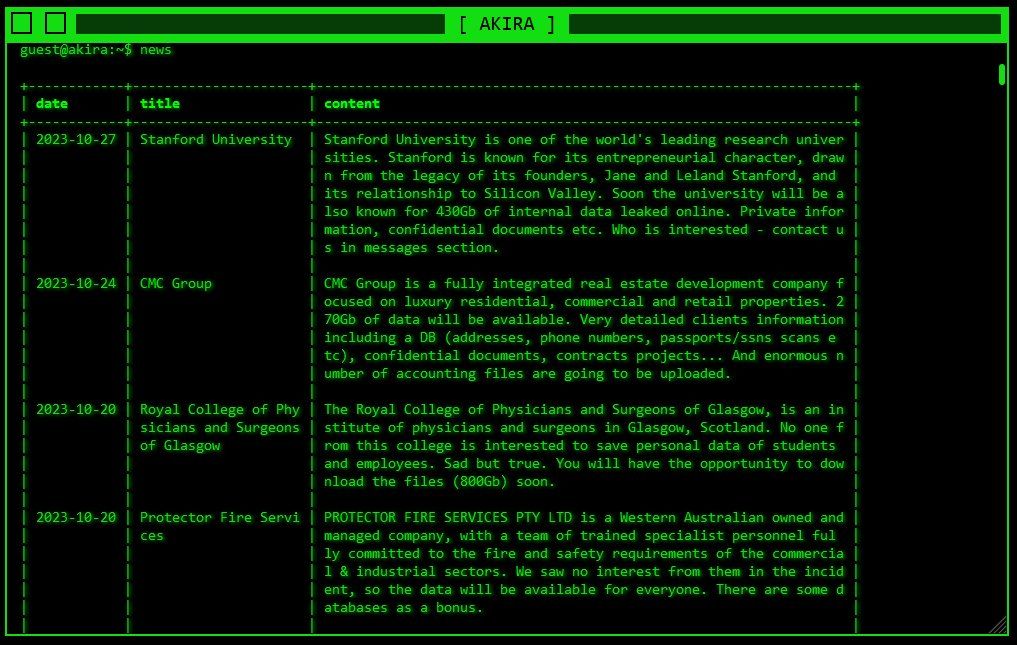
The note doesn’t specify the ransom, but the attackers are likely already negotiating a price with the University. According to reports, Akira sometimes demands outrageous sums, up to $4 million.
It’s unclear just how sensitive the impending data leak would be, if negotiations between the hackers and the victims fail. The SUDPS is known to handle case reports, risk evaluations and crime reports involving students, faculty and other community members. Serving a plurality of high-profile figures, the University may well be tempted to negotiate with their aggressors.
In a statementissued Friday, the department said it was “continuing to investigate a cybersecurity incident at the Stanford University Department of Public Safety (SUDPS) to determine the extent of what may have been impacted.”
“Based on our investigation to date, there is no indication that the incident affected any other part of the university, nor did it impact police response to emergencies.,” according to the notice. “The impacted SUDPS system has been secured.”
“Our privacy and information security teams have been giving this matter their concerted attention, in coordination with outside specialists,” the notice continued. “The investigation is ongoing and once it is completed, we will act accordingly and be able to share more information with the community.”
Akira is believed to be an offshoot of the former Conti operation, with the actual malware deployed onto victims’ systems sharing similarities in code. The hackers don’t discriminate between victims, hitting even the healthcare sector, if given the opportunity.
In a security bulletin issued in September, the US Department of Health and Human Services Health Sector Cybersecurity Coordination Center (HC3) drew attention to Akira’s attacks on healthcare institutions.
Depending on the nature of the data involved, Stanford may resort to paying ransom to keep the data safe. However, paying doesn’t mean Akira will delete the data and leave the University off the hook. As with other ransomware cases, Akira might try to extort them again in the future, or they still might sell the data to the highest bidder in closed hacking circles on the dark web.
tags
Author
Filip has 15 years of experience in technology journalism. In recent years, he has turned his focus to cybersecurity in his role as Information Security Analyst at Bitdefender.
View all postsRight now Top posts
Most People Still Write Important Passwords Down, Bitdefender Report Finds
June 07, 2024
1 in 4 Consumers Faced a Security Incident in the Last Year, Bitdefender Report Shows
June 03, 2024
Steam Trades Scam – Be Ready for Anything If You Sell or Buy Via Steam Marketplace
May 31, 2024
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








